Payload Extraction for Reverse engineering
and
Exploitation Infrastructure Mapping
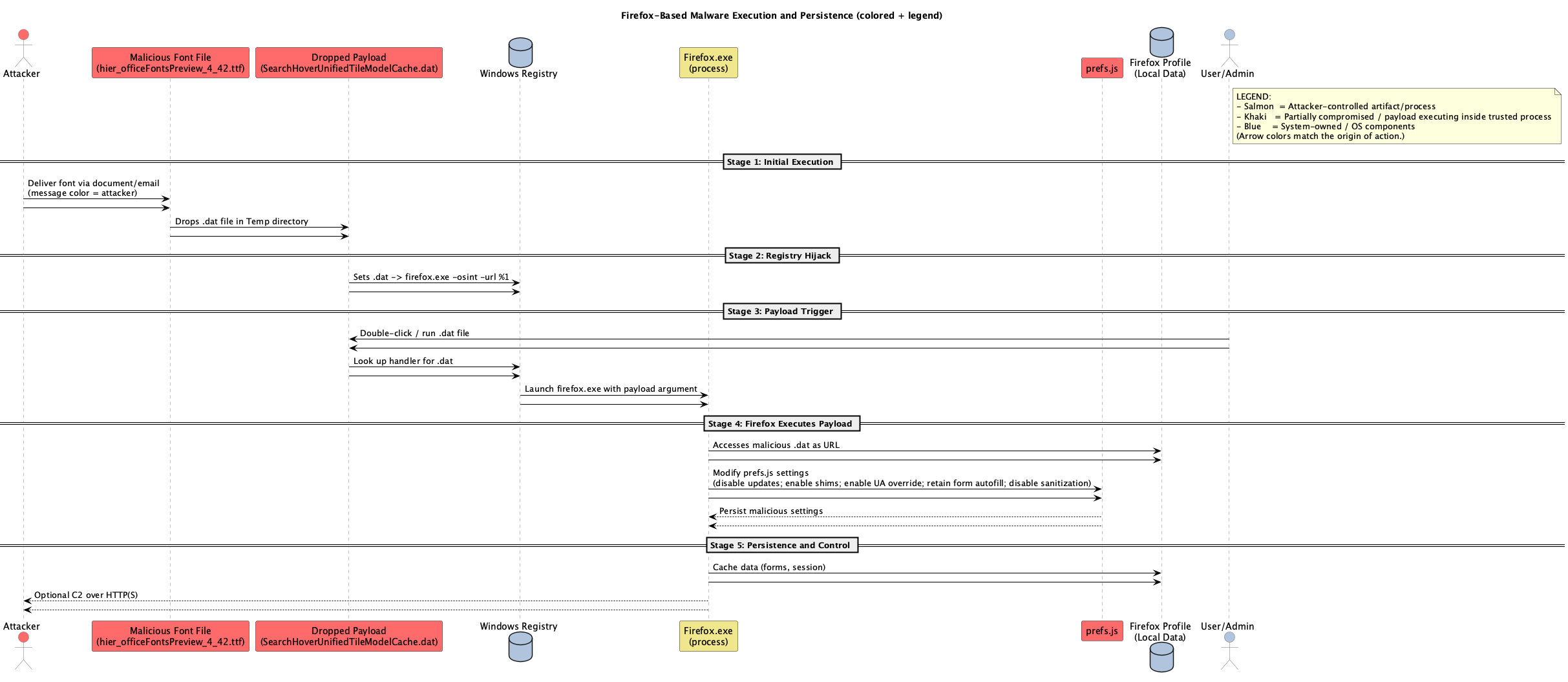
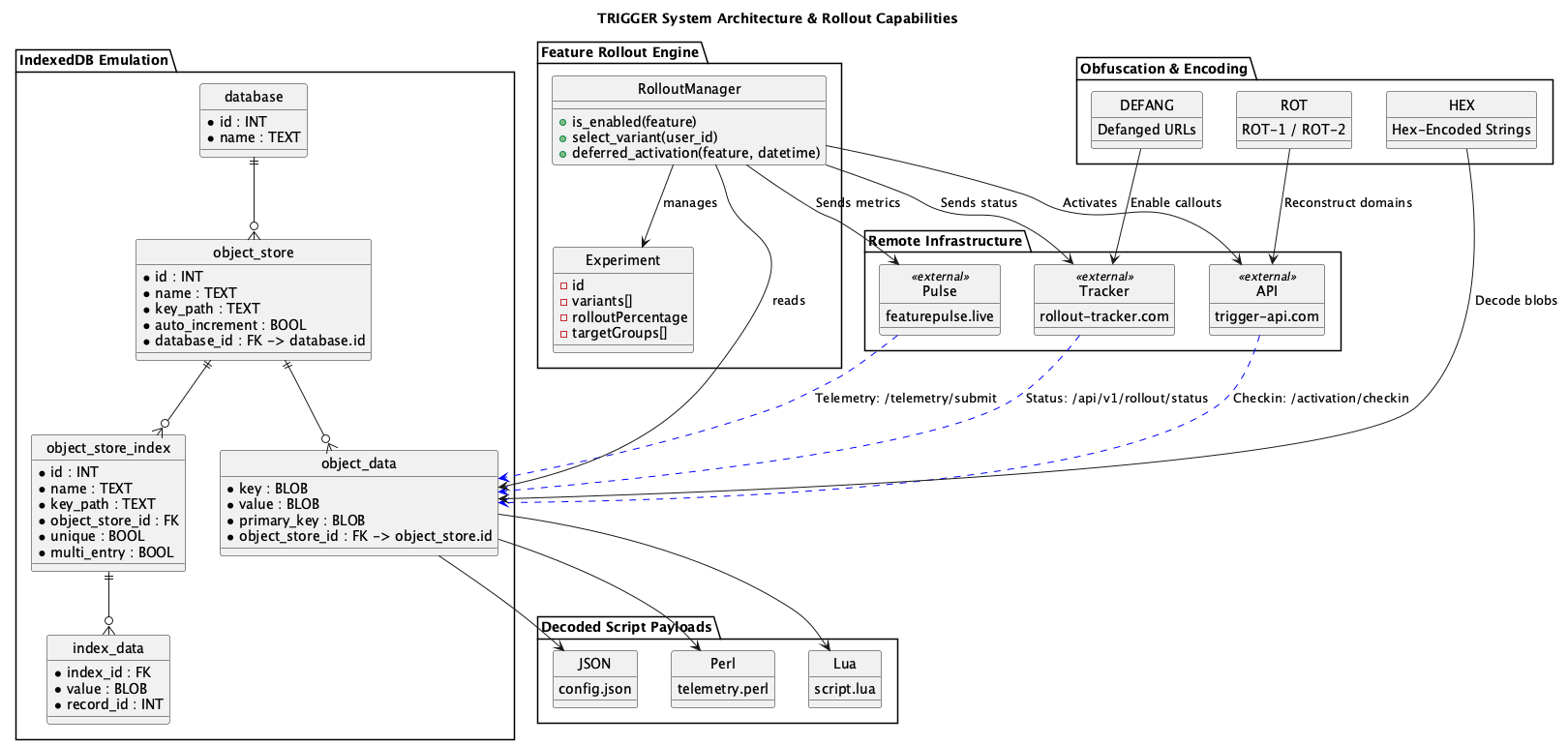
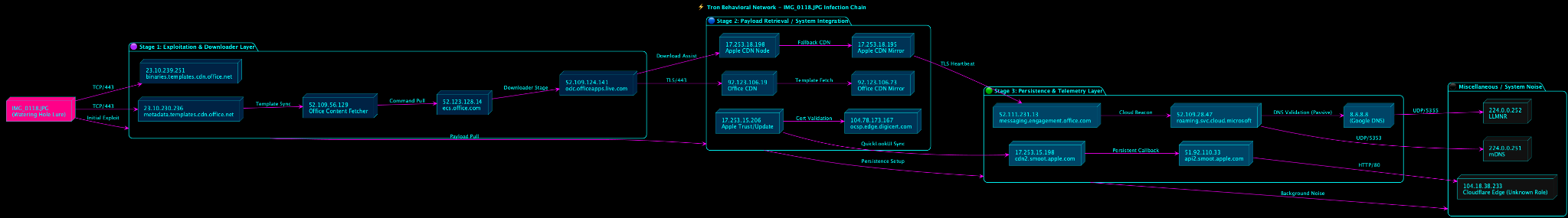
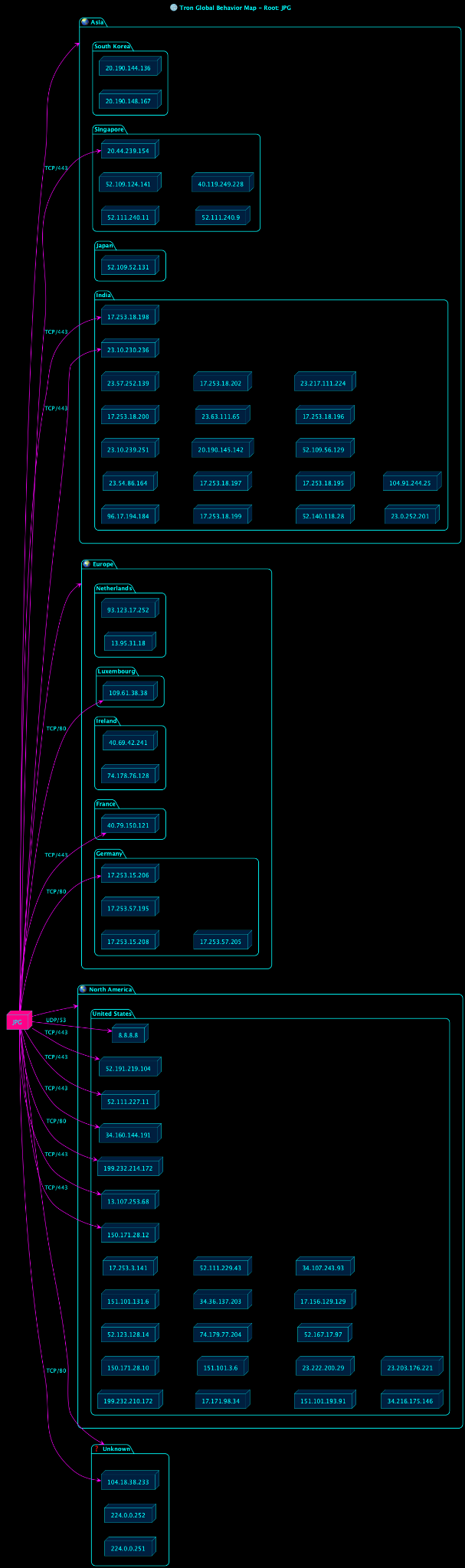
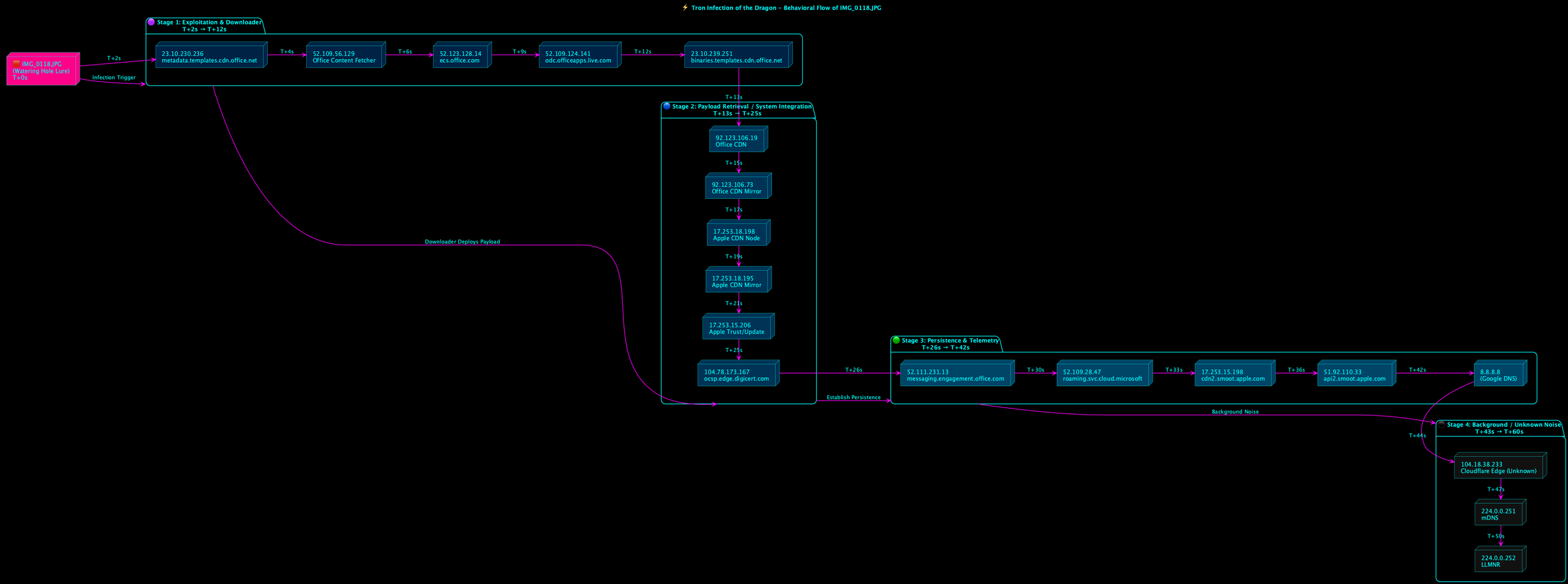
It all began with a text in 2025. It was a text message with a malcrafted image with the recently publicly released Proof of Concept of CVE-2025-43300, but it was with live malware that was able to web itself across the internet and extract down to 1337_TECH cellular phone. The obvious thing would have been to delete the message. Instead I went and wanted to demonstrate and prove to myself it was benign. Instead After recording PCAPS and using my own detonation servers I was able to identify the web that spanned across multiple continents and several countries.
At the end, make a nice concise picture of how modern APT groups are taking control of targeted computers and networks, that is from shadow firefox profiles for stealth insertion and exfiltration, as well as persistence. It is a beautiful masterpiece of software engineering to be able to produce an offensive operation such as the one I found.
If the operation is the rose bush then what is not so beautiful is the thorns protecting this rose bush. That is to say it has poison tipped thorns, waiting for it’s victim. This is not your average ransomware gang, that is for certain, but of a highly sophisticated more then state-sponsored or Nation State affiliated hackers.
Cryptographic Vaults to Counter Q-Day
Advanced Software Systems Engineering and Applied Detection Engineering
Advanced Research ranging from Detection Engineering to Cryptographic Vaults.
Systems of Systems Machine Learning Research, and Needle in the Haystack Breakthroughs applied in Bug Hunting with custom Machine Learning - Tooling. Reproducible and Explainable Theories to enhancing the Vulnerability Researcher towards more Productization
1337_TECH’s
brand vision
1337_TECH is my open source projects driven by curiosity, creativity, and code. My mission is to explore the edges of technology, and educate the interested public, on embedded systems and kernel development; to cybersecurity research and secure network architecture. 1337_TECH builds tools that empower individuals to learn, experiment, and defend in an increasingly complex digital world.
What started as my late night experiments in firmware emulation and Linux kernel hacking and hardening has evolved into I making an effort to create transparent, high quality software for education and innovation. Every software release reflects a commitment to craftsmanship, clarity, and security, not perfect, but progression, whether it’s a Zero Trust SOHO router Linux-RT based Operating System, an Recurrent Neural Network based steganography engine, or an open debugging framework built on QEMU and Ghidra.